Introduction
As cryptocurrencies continue gaining popularity, finding secure storage solutions for your digital assets has become increasingly important. Cryptocurrency wallets are software or hardware devices that store, manage, and transfer cryptocurrencies like Bitcoin and Ethereum. Security is a major concern regarding cryptocurrency, especially given the rising prevalence of cybercrime.
To protect your assets from theft or loss, it's essential to choose the right type of wallet and implement proper security measures. In this article, we'll explore the different types of cryptocurrency wallets, the security measures you can take to safeguard your assets, and the best practices for using cryptocurrency wallets. Whether you're new to cryptocurrencies or an experienced investor, understanding how to secure your digital assets is crucial. So let's dive into cryptocurrency wallets and learn how to protect your investments.
Fundamentals of Cryptocurrency Wallets: Private Keys and Seed Phrases
Every cryptocurrency wallet has a private key, a unique alphanumeric code that allows you to access and manage your funds. Your private key gives you ownership and control over your cryptocurrencies. It's important to keep your private key safe and never share it with anyone, as losing it means losing access to your funds, which cannot be recovered.
To safeguard your wallet, you should also create a seed phrase, also known as a recovery phrase or backup phrase. Your seed phrase is a list of words that can be used to restore your wallet in case your device is lost, stolen, or damaged. Seed phrases are usually composed of 12 or 24 words in a specific order, essential for generating your private key. Because anyone with access to your seed phrase can generate your private key and gain access to your funds, it's critical to store your seed phrase in a secure location, such as a fireproof safe or a safety deposit box. Understanding the fundamentals of private keys and seed phrases is critical to ensuring the security and accessibility of your cryptocurrency assets.
Seed phrases and private keys are both important components of cryptocurrency wallets, and they are closely related. A seed phrase is a list of words used to generate a private key, a unique code that provides access to a particular cryptocurrency wallet. The process of generating a private key from a seed phrase is known as hierarchical deterministic (HD) wallet derivation, which is specified in BIP29 (Bitcoin Improvement Proposal 29). Essentially, the seed phrase serves as a "master key" that can be used to regenerate the private key at any time, even if it is lost or stolen. This makes it easier for users to manage and recover their funds in the event of a wallet-related issue. Seed phrases and private keys are crucial to cryptocurrency security and should be kept confidential and stored safely.
Cold Wallets vs. Hot Wallets
There are two primary categories of cryptocurrency wallets: cold and hot. Cold wallets store your private keys on a device not connected to the internet, making them less vulnerable to hacking and online attacks. Hardware wallets, paper wallets, and brain wallets are all examples of cold wallets. Hardware wallets, which come in the form of USB drives that you can plug into a computer or smartphone, are the most popular.
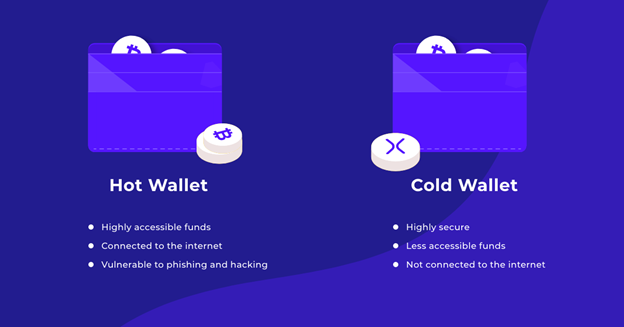
Hot wallets, on the other hand, are connected to the internet, which makes them more convenient to use but also more vulnerable to security breaches. Hot wallets include mobile wallets, web wallets, and desktop wallets. Mobile wallets are apps that you can download on your smartphone and provide you with easy access to your cryptocurrencies on the go. Web wallets are online platforms that store your cryptocurrencies and allow you to access them anywhere with an internet connection. Desktop wallets are software programs that you install on your computer. While hot wallets are more convenient to use, they're also more vulnerable to security breaches. Cold wallets offer a higher level of security but may be less convenient to use. Choosing the right type of wallet depends on your needs and risk tolerance. To protect your digital assets, choose a reputable wallet provider, enable two-factor authentication, and keep your private keys and seed phrases safe.
You can also connect your cold wallet to a hot wallet like Metamask. Connecting a cold wallet to a hot wallet like Metamask involves a few steps to ensure the security of your cryptocurrency assets. First, ensure that your cold wallet is compatible with the hot wallet and can be added as a supported account. Then, you must connect the two wallets through a bridge or a compatible integration. For example, you can use a hardware wallet bridge like the Ledger Live application to connect your Ledger cold wallet to Metamask. Once the connection is established, you can transfer cryptocurrency assets from your cold wallet to the hot wallet for use in decentralized applications or trading. It is important to note that when connecting a cold wallet to a hot wallet, you should be cautious of potential security risks such as phishing scams or malware attacks. Always verify the authenticity of the connections and ensure that your private keys remain secure.
Best Practices for Secure Cryptocurrency Storage
To ensure the security and accessibility of your digital assets, it's essential to follow best practices for using hot and cold wallets. Here are some tips to help you keep your cryptocurrencies safe:
For hot wallets, choose a reputable wallet provider and use strong passwords. Enable two-factor authentication to add an extra layer of security to your account. Avoid using public Wi-Fi when accessing your wallet, and be cautious when making online transactions. It's also a good idea to keep only a small amount of cryptocurrency in your hot wallet for everyday use and store the bulk of your digital assets in a cold wallet.
For cold wallets, keep your device in a secure location, such as a fireproof safe or a safety deposit box. Always keep your seed phrase safe and never share it with anyone. Regularly back up your wallet to prevent the loss of your private keys. It's also a good idea to use a hardware wallet for cold storage, as it provides an extra layer of security. Hardware wallets like Ledger Nano X, Trezor Model T, and KeepKey are popular options that offer a high level of security.

In summary, choosing the right type of cryptocurrency wallet and implementing proper security measures is crucial for protecting your digital assets. Understanding the fundamentals of private keys and seed phrases, as well as the pros and cons of different types of wallets, is essential for minimizing the risks associated with cryptocurrency storage. By following best practices, such as choosing a reputable wallet provider, enabling two-factor authentication, and keeping your private keys and seed phrases safe, you can keep your digital assets secure and accessible.
Conclusion
In conclusion, cryptocurrency wallets are essential for managing and storing digital assets like Bitcoin, Ethereum, and other cryptocurrencies. However, the security of your cryptocurrency assets is a major concern, given the increasing prevalence of cybercrime. To safeguard your digital assets, it's crucial to choose the right type of wallet, implement proper security measures, and follow best practices for using hot and cold wallets. By understanding the fundamentals of private keys and seed phrases and the pros and cons of different wallets, you can minimize the risks associated with cryptocurrency storage and keep your digital assets safe. Whether you're a new user or an experienced investor, following these guidelines can help you confidently protect your investments and navigate the cryptocurrency world.
Discover SynFutures' crypto derivatives products: www.synfutures.com/.
Disclaimer: SynFutures Academy does not guarantee the reliability of the site content and shall not be held liable for any errors, omissions, or inaccuracies. The opinions and views expressed in any SynFutures Academy article are solely those of the author(s) and do not reflect the opinions of SynFutures. The SynFutures Academy articles are for educational purposes or information only. SynFutures Academy has no relationship to the projects mentioned in the articles, and there is no endorsement for these projects. The information provided on the site does not constitute an endorsement of any of the products and services discussed or investment, financial, or trading advice. A qualified professional should be consulted prior to making financial decisions.


